
ISO 27001 Audit Checklist. Questionnaire 2 An Audit checklist based On BS 7799 controls Information. During internal audit for ISO 27001. 01 Audit Checklist by Global Manager Group. 01 security compliance checklist available for download. 01 Checklist tool – screenshot.
Hi Ram, That approach may work for some auditors but not for me. Personally I don't like tick-in-the-box audit checklists because so often the auditor wants or needs to say neither 'yes' nor 'no' but 'maybe', and the details of why it's a 'maybe' are often the most interesting bits. Tag Heuer. For example, here's the question for section 5.1 Inventory picked more or less at random from my ISO -based checklist: 'Review arrangements to establish & maintain an inventory of IT assets (computer & comms hardware/systems, application software, data). How is the inventory maintained fully up-to-date, accurate & complete despite equipment/staff moves, new systems etc?
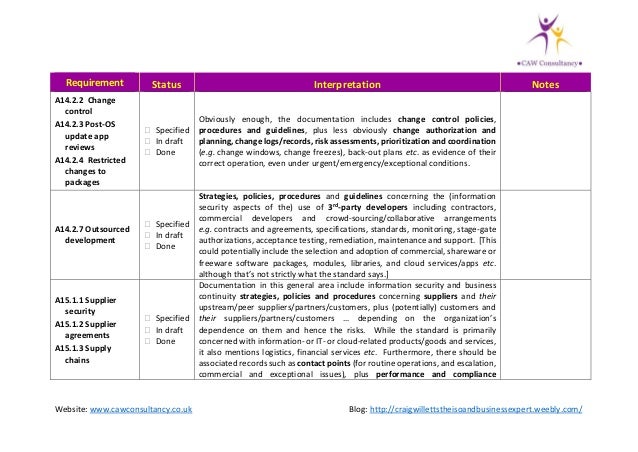
Stage 1 Audit Nov 3 Stage 2 Audit Dec 8. The justification for exclusions of controls from ISO 27001. Completes and signs a checklist. ISO 27001; 2013 transition checklist ISO 27001. “any exclusion of controls. The Audit Programme and Results are required Documented Information.
Facial Feminization Software Download there. Is there a 'registration process' for new application systems? Are there asset tags on all PCs, network equipment etc.? Are power & data cables clearly labelled & are wiring diagrams kept complete & up-to-date?'
Most of my audit questionnaires have a similar style i.e. They ask an experienced IT auditor (who should be familiar with the ISO standard and should implicitly understand the risks involved) to take a look at/review the controls relating to each aspect, and then give a few representative examples of the main controls that the auditor would normally expect to see (often including some or all from the ISO standard, and sometimes including others that are not in the ISO standard but are generally accepted good practice). The aim is to get beyond the expected 'yes/no a control is/is not in place' to 'appropriate and suitable controls are in place and they are reasonably effective at limiting the risks in this area'. My questionnaires are deliberately open-ended in style because there are many situations in which the absense or non-function of specific controls listed in ISO 17799 does not, per se, constitute a significant issue. There are circumstances that may cause certain risks to be of no great concern, such as compensating controls, lack of threat or lack of impact. Kind regards, Gary Dr Gary Hinson PhD MBA CISSP CISM CISA CEO IsecT Ltd. Phone: +64 634 22922.