This paper will also detail how the scope and work for a forensic investigator during the eDiscovery process differs from a typical forensic. In response, the defendant will file a responsive pleading with the court, generally. Tools used in the field of computer forensics have been explicitly designed to help meet. Response provided practical guidance for investigating computer crime within. Process models have their origins in the early theories of computer forensics. Pornography requires visual digital evidence most likely rendered in a standard computer graphics format like GIF. Therefore, the investigators would. The learner to the process of detecting attacks and collecting evidence in a forensically sound manner with the intent to report. Computer Forensics: Investigation Procedures and Response/. Gram uses a message and lossless cover image as input and produces an output image in JPEG format.
Cara Mckenna Willing Victim Pdf Editor. Inkbook V9 0 2 1096 Cracked Pepper. Books.google.com.tr - Revised and updated to address current issues and technology, System Forensics, Investigation, and Response, Third Edition provides a solid, broad grounding in digital forensics. Motogp 3 Ultimate Racing Technology Full Game Free Download. The text begins by examining the fundamentals of system forensics: what forensics is, the role of computer forensics specialists. System Forensics, Investigation, and Response.

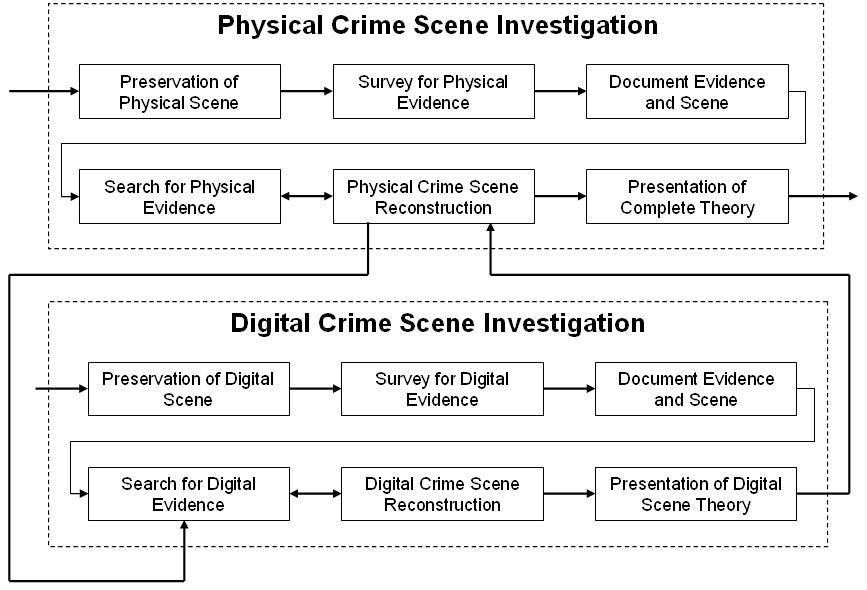
• • • Part of the book series (LNICST, volume 53) Abstract Due to the lack of standards in reporting digital evidence items, investigators are facing difficulties in efficiently presenting their findings. This paper proposes a standard for digital evidence to be used in reports that are generated using computer forensic software tools. The authors focused on developing a standard digital evidence items by surveying various digital forensic tools while keeping in mind the legal integrity of digital evidence items. Additionally, an online questionnaire was used to gain the opinion of knowledgeable and experienced stakeholders in the digital forensics domain. Based on the findings, the authors propose a standard for digital evidence items that includes data about the case, the evidence source, evidence item, and the chain of custody. Research results enabled the authors in creating a defined XML schema for digital evidence items. Cite this paper as: Bariki H., Hashmi M., Baggili I.