How To Decrypt Apco 25 Encryption Algorithms. The scenario is that you are the attacker and want to find out the secret key stored inside the board. There are some references to breaking encryption on a P25 system that I have come across. I've managed to decode police TETRA communications but the speech is scrambled so about all you can tell is the gender of the radio operator. More likely to be DMR or APCO P25 in the States. Hardware scanners such as the Uniden BCD996T offer APCO P25 functionality but software-defined radio (SDR) offers significantly improved flexibility. For example, software radio approaches can receive many channels at once, handle both voice and data (including the trunking control channel), decrypt encrypted traffic. Validated FIPS 1. 40- 2 Cryptographic Modules. Overall Level: 1- Physical Security: N/A - Mitigation of Other Attacks: N/A - Tested Configuration(s): Tested.
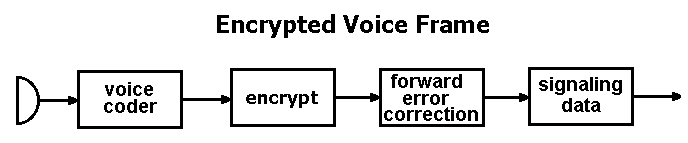
Security can a key aspect of public-safety communications, but (P25) system managers should establish policies to help ensure that encryption is used only when necessary, P25 network veterans said during a best-practices workshop in Washington, D.C., sponsored. While encrypted communications are vital for some specialized personnel—for example, members of SWAT teams, bomb squads and narcotics operations—it is not advisable to use encryption for all public-safety communications, according to Craig Jorgensen, former president of the P25 steering committee. Allison Doc 10 Keygen. “Encryption was never intended to be a ubiquitous tool that everybody has; if everybody’s got it, there no longer is the security element that you want,” Jorgensen said. “Encryption was intended for high-security risks, not just day-to-day traffic.
The cost of encryption is not only the economic costs but the cost of the spectrum that you’re using to perform the encryption, and there’s still a minor degradation [of voice quality] in encryption. “So, encryption shouldn’t be dealt with as an option, like a green light or a blue light. [You should look at] why I need it, how much am I willing to pay for it, and who really needs it.” Another issue with encryption is that it is not always possible to coordinate the security feature with other jurisdictions that may provide help during an emergency, according to Allen Holder, director of Lincoln County 911 Center in West Virginia. “If you encrypt too much, you may make your network so secure that you lose the benefit of,” Holder said.
This sentiment was echoed by several participants, with some noting that they have policies against using encryption on mutual-aid channels. There was a general consensus that public-works and public-service employees do not need encryption capabilities on their radios, but encryption usage for non-specialized public-safety organizations varied significantly between the participants. “I put encryption in all my equipment and components in the statewide system, because I was told that everything had to be encrypted in 1999,” said Paul Leary, chief of communications for the state of New Hampshire. “Fourteen years later, I have yet to have to use an encrypted channel in my department.